gmail forums exploded
12


















12
|
The new gmail in box, compose, and forcing hang outs on you has caused lots of threads likeproductforums.google.com/forum/#!topic/gmail/yl_XPO5Hw6Y[726-750-false] ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: gmail forums exploded
|
I switched to an IMAP client (T-Bird) 3 days ago when their latest nonsense started. Gillian Densmore wrote:
============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
|
You can also get back the classic/legacy gmail by using IE 8 or firefox 4 - both of wich are slighly faster for general websurfing compared to the most recent/modern versions.
That being said what else is out there for webmail?
Gmail has some relatively good street-cred. Wich is hard to compete with when saying to someone: oh send me mail to my skydrive acount-for example.
On Fri, Aug 16, 2013 at 9:13 PM, Sarbajit Roy <[hidden email]> wrote:
============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
TLS encryption [was gmail forums exploded]
|
In reply to this post by Sarbajit Roy (testing)
On 8/16/13 9:13 PM, Sarbajit Roy wrote:
Speaking of e-mail providers, I've noticed that a some of my providers don't provide TLS encryption. Can anyone suggest one that passes http://www.checktls.com/? The usual suspects are surely all PRISM-equipped by now, so I was thinking of something off the beaten path. ;-) Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
Some quick tests.
From a few sites off the top of my head, it seems that e-mail in transit is more secure if one uses regional ISPs.. Big companies: Gmail, yes (but named in PRISM slides) Hotmail, no Yahoo, no Earthlink, no Comcast, no Apple's icloud.com, no Regional ISPs Cybermesa, yes SWCP, yes web-ster.com, yes ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Marcus G. Daniels
try
https: // ecomail DOT at On 8/17/13, Marcus G. Daniels <[hidden email]> wrote: > On 8/16/13 9:13 PM, Sarbajit Roy wrote: >> I switched to an IMAP client (T-Bird) 3 days ago when their latest >> nonsense started. > Speaking of e-mail providers, I've noticed that a some of my providers > don't provide TLS encryption. > Can anyone suggest one that passes http://www.checktls.com/? > ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
On 8/17/13 12:05 PM, Sarbajit Roy
wrote:
That server does do TLS, and there's AES-256 encryption on the site itself.try https: // ecomail DOT at Looks like he is a likely to be an actual person.. :-) http://muenchen.piratenpartei.de/author/muenchen/ Of course, for U.S. citizens, using an overseas account could mean jumping out of the frying pan and into the fire! Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
Marcus, et al -
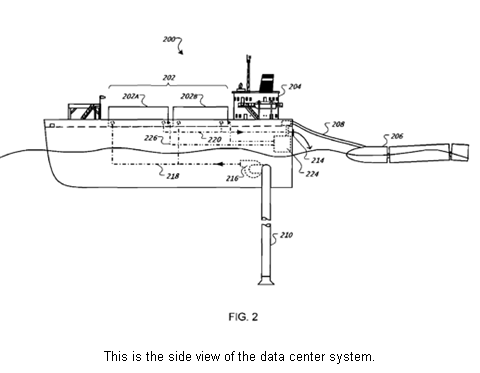
Of course, for U.S. citizens, using an overseas account could mean jumping out of the frying pan and into the fire!Especially those with security clearances working at national scientific laboratories? Lavabit's guy pointed out that trying to provide encrypted e-mail services *with* (geographic) ties to the US was a *very bad idea*... so you make a very good point... if you go *offshore* for your encrypted e-mail services you are *inviting* the NSA to intercept, record, (attempt to) decrypt, read, etc. your e-mail. Of course, now that it is accepted that they don't need for you to be presumably communicating with a foriegn entity to do the same, then "why not?" ... The analogy of "needle in a haystack" has already been used. It seems as if using overtly encrypted e-mail services is like putting your needle in a somewhat difficult to open envelope. It makes it easier to find the needles (because they are now in easily identifiable envelopes) but harder to read (open) them? Maybe the Zuni or the Basque peoples will all join EFF and offer their services as code-talkers? Where's Homer Kaywumptewa when you need him (one of my father's Zuni friends while I was growing up)? Whatever happened to Google's "Offshore Data Centers"? https://sites.google.com/a/opensailing.net/protei/news/googlespatentforunderwaterdatacenter Steganography is where the future lies. In case you wonder why my e-mails are always so long and circuitous... it provides more signal to act as noise to hide the real signal in (hardly). - Steve What a tangled web we weave!
============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
All that being said, I do use SSL/TLS for my e-mail client (T-Bird via
IMAP) to a regional (SWCP) mail service. This (probably) means that anyone intercepting (sniffing my wireless, tapping my first mile provider, backbone, etc.) will only get medium-high entropy bitstreams. But I don't encrypt my hard drive, nor does, I presume SWCP. I don't insist on encrypted conversations with anyone, so I'm only one tiny step more "secure" than I would be if I didn't use SSL/TLS with my ISP mail server. I suppose if we all insist on encrypted e-mail as the standard we increase the size of the pile of envelopes with needles in them. It might help some... but this feels a lot like an arms race. - STeve ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Marcus G. Daniels
Any reason to believe that SWCP/Cybermesa are not PRISM-equipped? HOw do we (even) know that checktls.com isn't some kind of honeypot, trying to get us to signal our potential riskiness by using it to test our e-mail service? And how do we know that what checktls reports is even accurate? How do we discover whether THEY are trusted/trustable? - STEVE ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Steve Smith
I loved the defense offered in http://www.nytimes.com/2013/08/17/us/nsa-calls-violations-of-privacy-minuscule.html, that 2776 mistakes in a year were nothing to get excited over, they're making 20 million queries a month. I wonder when we were going to find out that number in the normal course of events. -- rec -- On Sat, Aug 17, 2013 at 2:19 PM, Steve Smith <[hidden email]> wrote: All that being said, I do use SSL/TLS for my e-mail client (T-Bird via IMAP) to a regional (SWCP) mail service. This (probably) means that anyone intercepting (sniffing my wireless, tapping my first mile provider, backbone, etc.) will only get medium-high entropy bitstreams. ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Steve Smith
On 8/17/13 2:10 PM, Steve Smith wrote:
There should be no reason to go overseas and make appearances suspect, because we all have the right to do this in our personal affairs. Using adequate encryption and processes means that those `making mistakes' at or on behalf of the NSA will be forced to go to the trouble to warrant the relevant ISP to install intercept hardware. I expect it to be as hard as the law says it should be. At the very least there is time and effort involved in that. And if the mail servers are owned the user, then they need to seize the owner's hardware with a proper warrant and/or coerce the owner to hand over the encryption keys. This situation is not at all like the `Police are issued guns but don't misuse them' analogy because a gun that is fired at someone results in an undeniable outcome. In contrast, this is all in the shadows and deniable. If everyone exercises their right to use strong encryption, all the way to the storage medium, using open, auditable open source code, this whole issue goes away. It's just that we're not there yet, so they are trying these annoying PRISM technical tricks to interleave taps. If people aren't emphatic about this, we'll slide toward the Clipper chip nonsense and key escrow. Government employees using government systems have to live with that, as do many people working at various sorts of corporations, but random U.S. citizens do not -- at least not yet. Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Steve Smith
On 8/17/13 2:32 PM, Steve Smith wrote:
HOw do we (even) know that checktls.com isn't some kind of honeypot, trying to get us to signal our potential riskiness by using it to test our e-mail service?You can do it by hand, it's just a convenience. They pretty much show you the (e.g. telnet) commands to use. I just mentioned that URL in the hopes someone would say "Mine ISP does!" so that I could give them my money instead. Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Roger Critchlow-2
On 8/17/13 2:37 PM, Roger Critchlow
wrote:
It probably measures something. Like the number of middle managers that they have with a conscience. If as a group they perceive risk as inaction, it could be a small fraction of the actual violations. Someone had the presence of mind to realize that they needed to have some plots on some sort of violation, so that it would seem like they were doing something proactive about an obvious risk when a trouble-making Senator came along, etc. Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Marcus G. Daniels
Marcus -
I understand that I can check the handshakes, transmissions, etc by hand (telnet or a simple program I write myself)... what I'm offering is that I don't know how to tell that checktls.com isn't a honeypot, looking for people who "act guilty" by trying to secure their communications. Sure it can actually do the tests it claims it is doing, and maybe even be accurate in all cases except maybe one where the nefarious shadowy guys in the background already "have your number" and the shadowy characters instruct the system to report tighter security than exists, causing the suspect to leave themselves more vulnerable than they thought, etc... yes, these are the fruits of a paranoid mind, but just because you are paranoid, *doesn't* mean they aren't out to get you. MY ISP DOES! and it's regional and I like them (over 15 years now) and I trust them (right up to the point when they get a National Security Letter instructing them to quietly and without telling anyone including their lawyer do exactly what they are told on pain of secret charges of treason, etc.). I also have no reason to believe that they keep my e-mail encrypted... and from what I'm hearing from lavabit, if they did, THEY TOO would be facing what lavabit is? - Steve
============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
On 8/17/13 3:35 PM, Steve Smith wrote:
Public advocacy for having ubiquitous secure transfers is a stronger signal for them to contemplate. yes, these are the fruits of a paranoid mind, but just because you are paranoid, *doesn't* mean they aren't out to get you.Speaking of paranoia, here's a little Thunderbird add-in that aims to check that all of the e-mail hops were secure. It's a little buggy, but a nice idea (double check its work if it gives you a happy face). https://addons.mozilla.org/en-US/thunderbird/addon/paranoia/ Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
Marcus
> Public advocacy for having ubiquitous secure transfers is a stronger > signal for them to contemplate. Agreed. >> yes, these are the fruits of a paranoid mind, but just because you >> are paranoid, *doesn't* mean they aren't out to get you. > Speaking of paranoia, here's a little Thunderbird add-in that aims to > check that all of the e-mail hops were secure. It's a little buggy, > but a nice idea (double check its work if it gives you a happy face). I get happy faces over the strangest things... and in fact, I like highwire work without checking the net before I go up... it just feels like bad juju. It is merely important (to me) to know that I *can* check the net if I choose to... that it is checkable and I am competent to do so and nobody gets too wIerded out if I do. > > https://addons.mozilla.org/en-US/thunderbird/addon/paranoia/ - Steve ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
Administrator
|
On Haystacks: There are two types of cracking that can occur to an individual
1 - Targeted: The bad guy (NSA, a malicious cracker...) is after you specifically. 2 - Non-Targeted: The bad guy casts a broad net, or inspects a big haystack, for exposed individuals
If 1), your chances are really low of avoiding being hacked unless the bad guy is novice.
2) is a double edged sword. Being concerned about encryption email routing and storage has merit if the trolling is simply putting up a wall, saying "move along, nothing here". But it also puts up a sign saying "I have a reason to hide"
My guess is that all of us using any sort of extra measures, such as encryption, are definitely on the NSA books.
-- Owen
On Sat, Aug 17, 2013 at 5:35 PM, Steve Smith <[hidden email]> wrote: Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
On 8/18/13 9:02 AM, Owen Densmore
wrote:
One can imagine a Linux distribution that is purpose-built for Lavabit-like e-mail, but easy to install and maintain, like Tor is. Individuals could run it on home systems. That way, victims of the PRISM program would know when it happened because the FBI would have to come to their house to take their stuff. When they insisted on the keys, they could be cheerfully provided -- in my case showing them the whole gamut of pictures of my dogs and my many open source build trees! Perhaps RAID 1 or similar so that they can take half the drives, but you can continue to work. I guess they are sort of humorless and would want to take the whole thing. Oh well. Marcus ============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
Re: TLS encryption [was gmail forums exploded]
|
In reply to this post by Owen Densmore
So... here's a paradox... or is it a
conundrum:
I choose to live in a world with as little fear or paranoia as possible (some may not see that from my postings here, but I claim it to be true). So, to secure my wireless network, to encrypt my e-mail, to encrypt my hard drive, to use obfuscating proxies in my network/computer life would be to invite a much more dangerous and scary world in than I want to live in. Just as adding deadbolts to my doors at home or putting a lo-jack in my vehicle, or keeping a loaded gun in my bedstand would feel like inviting in the bad things they are supposed to keep out. I've lived decades without any of those and I can't say I have any significant reason to feel like a chump about it, while I know folks (there may be some here) who are pretty sure that if they didn't shoot their triple-deadbolt and set their "armed response" security system every time they go through their door, that they would be victim of home invasion, etc. On the other hand, I understand the logic of wanting erstwhile criminals to assume that "everyone owns a gun and knows how to use it", and the logic of sending private communication by sealed envelope, or using SSL/TLS for e-mail (and other) communication over an otherwise open network. So is there a "best of both worlds"? I try to strike this by leaving my wireless network open to use by "anyone", but setting up my e-mail client with SSL/TLS and only sending sensitive information over the web via https . I can imagine using the disk-level encryption provided on my system as a matter of course, but I *can't* imagine setting up an obfuscating web proxy and insisting that all my co-mmunicants decrypt my e-mails with PGP, etc. This all smacks so strongly of immune systems and complex population/prey/symbiote/parasite communities that I feel like I need to go back and review Stephanie Forrest's work again.
============================================================ FRIAM Applied Complexity Group listserv Meets Fridays 9a-11:30 at cafe at St. John's College to unsubscribe http://redfish.com/mailman/listinfo/friam_redfish.com |
«
Return to Friam
|
1 view|%1 views
| Free forum by Nabble | Edit this page |